ChocoHax Backdoor Remover
DISCLAIMER: In the ChocoHax Hestia package, you can separately install a backdoor scanner/cleaner for "Cipher Panel" and/or similar tools, but the removal of all backdoors on the server is not guaranteed. Follow this tutorial for manual removal.
This tutorial is written to help users remove backdoors from their servers. We assume no responsibility for any damage caused by improper use of the provided information.
If your server is under attack from backdoors, it is very likely that scripts are being executed remotely by malicious users.
Your passwords may have also been compromised, so it is advisable to change all server access passwords.
Servers typically affected by backdoors have previously installed pirated/cracked or unsafe scripts.
Therefore, it is recommended to back up your data and reinstall the server from scratch.
Backdoors are persistent, meaning they may be reinstalled after removal. Therefore, it is advisable to monitor the server and only start it after it has been completely cleaned.
Steps to Remove Backdoors:
If you need support for backdoor removal, include the scan log in the ticket to facilitate our work.
For manual backdoor removal, follow these steps: (DO NOT RESTART THE SERVER UNTIL ALL BACKDOORS ARE REMOVED)
WARNING: If you are unsure of what you are doing, seek help from an expert or reinstall the server from scratch.
Some backdoors might be hidden inside obfuscated resources and/or protected by FiveM Escrow and cannot be detected by the scanner!
BE CAREFUL WHAT YOU BUY AND INSTALL ON YOUR SERVER!
Many shops offer scripts at very low prices, but these scripts may contain malware. Do not trust pirated or unsafe scripts!
DISCLAIMER: In the ChocoHax Hestia package, you can separately install a backdoor scanner/cleaner for "Cipher Panel" and/or similar tools, but the removal of all backdoors on the server is not guaranteed. Follow this tutorial for manual removal.
This tutorial is written to help users remove backdoors from their servers. We assume no responsibility for any damage caused by improper use of the provided information.
If your server is under attack from backdoors, it is very likely that scripts are being executed remotely by malicious users.
Your passwords may have also been compromised, so it is advisable to change all server access passwords.
Servers typically affected by backdoors have previously installed pirated/cracked or unsafe scripts.
Therefore, it is recommended to back up your data and reinstall the server from scratch.
Backdoors are persistent, meaning they may be reinstalled after removal. Therefore, it is advisable to monitor the server and only start it after it has been completely cleaned.
Steps to Remove Backdoors:
- Turn off your FiveM Server.
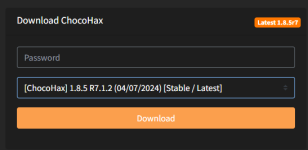
- Download and Install ChocoHax Hestia from ChocoHax Panel
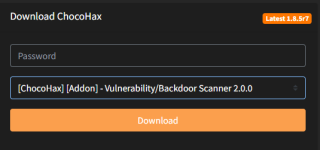
- Download and Install the "Vulnerability/Backdoor Scanner" Addon from ChocoHax Panel
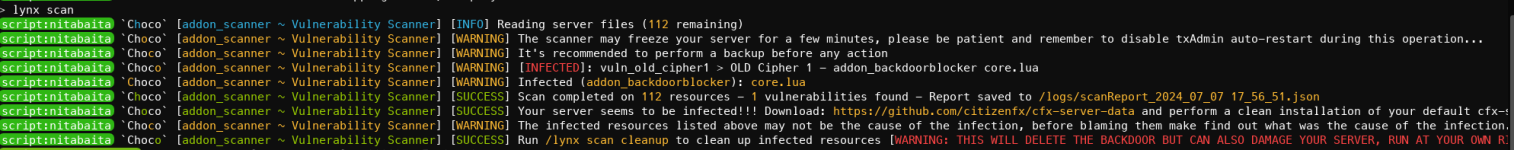
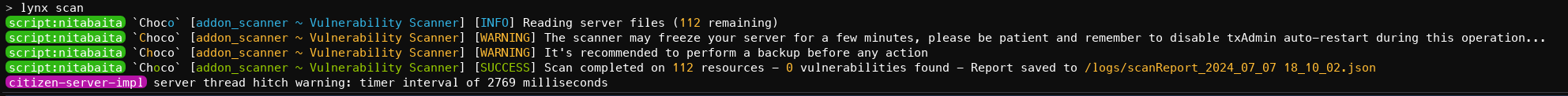
- Restart your FiveM Server and run a server scan with the command /lynx scan
- If backdoors are found, run the command /lynx scan cleanup to automatically remove the backdoors.
If you need support for backdoor removal, include the scan log in the ticket to facilitate our work.
JSON:
{
"resourcesScanned": 112,
"whitelistedResources": [],
"vulnerabilitiesFound": 1,
"infectedResources": [
"addon_backdoorblocker"
],
"scanMode": "quick",
"scanDate": "2024-07-07 17:46:15"
}For manual backdoor removal, follow these steps: (DO NOT RESTART THE SERVER UNTIL ALL BACKDOORS ARE REMOVED)
- After running the command /lynx scan cleanup, run another scan with the command /lynx scan to verify that all backdoors have been removed.
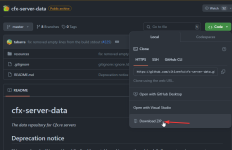
- Download a clean copy of the base FiveM resources from FiveM GitHub CFX-Server-Data (THIS STEP IS VERY IMPORTANT).
- Download clean artifacts from FiveM Windows Artifacts or FiveM Linux Artifacts.
- Overwrite the files on your server with the clean artifacts and resources.
- Change all server access passwords, database passwords, RCON passwords, and verify that your server.cfg file is clean.
- Restart the server, wait 2 minutes, and run the scan again with the command /lynx scan to ensure all backdoors have been removed.
WARNING: If you are unsure of what you are doing, seek help from an expert or reinstall the server from scratch.
Some backdoors might be hidden inside obfuscated resources and/or protected by FiveM Escrow and cannot be detected by the scanner!
BE CAREFUL WHAT YOU BUY AND INSTALL ON YOUR SERVER!
Many shops offer scripts at very low prices, but these scripts may contain malware. Do not trust pirated or unsafe scripts!
Last edited: